Network/System Administration:
 We have network engineers available to create local Intranets and Networks (ATM, Frame Relay, ISDN, TCP/IP, IPX/SPX), using the latest in technology. Whether WiFi, WAN, or LAN, we can help get it up and running; or maintain/upgrade a current network. (Now is the time to make sure your WiFi is utilizing optimal security). We are familiar with a wide array of Network hardware, including (but certainly not limited to): ACD, Channel Banks, CTI, Ethernet, Fast Ethernet Hubs/Switches, PC’s, PBS, Routers, Servers, Voice Mail, WAN/LAN, VRU, Compaq/DEC/HP Alpha Servers/Clusters/Raid Arrays, Compaq Proliant Servers, Sun Microsystems, HP Servers, Apple X Serve.
We have network engineers available to create local Intranets and Networks (ATM, Frame Relay, ISDN, TCP/IP, IPX/SPX), using the latest in technology. Whether WiFi, WAN, or LAN, we can help get it up and running; or maintain/upgrade a current network. (Now is the time to make sure your WiFi is utilizing optimal security). We are familiar with a wide array of Network hardware, including (but certainly not limited to): ACD, Channel Banks, CTI, Ethernet, Fast Ethernet Hubs/Switches, PC’s, PBS, Routers, Servers, Voice Mail, WAN/LAN, VRU, Compaq/DEC/HP Alpha Servers/Clusters/Raid Arrays, Compaq Proliant Servers, Sun Microsystems, HP Servers, Apple X Serve.
FSA handles large corporate clients, museums, and even smaller private networks. We do it all; from hard wiring, to setting up wireless access nodes. FSA is also fully experienced with: Unix, MAC OS X server, Script maintenance related to cluster configuration and redundancy, and Telephony services.
Systems Software Programming:
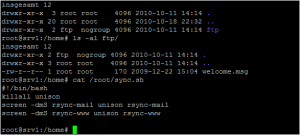 Installing, customizing and supported for IBM and OEM software in shared DASD and catalog environments. We are able to implemented assembler exits and user modifications. I/O-Genned hardware and configured LPARs. FSA can audit product usage to save licensing costs.
Installing, customizing and supported for IBM and OEM software in shared DASD and catalog environments. We are able to implemented assembler exits and user modifications. I/O-Genned hardware and configured LPARs. FSA can audit product usage to save licensing costs.
Our consultants have experience assuming group leadership, technical coordination, and project management responsibilities for S/390 and third-party software teams. Specialties: IBM: OS/390 and utilities through R10, MVS/ESA, HCD/IOCP, SMP/E, ServerPac, CBIPO/PDO, JES2, OS/390 UNIX., DFP, TSO, ISPF, REXX, RACF, SMS, L.E., COBOL II, RMF, IPCS, VSAM, GDDM, DITTO, VM. OEM: $AVRS, PDSFast, AbendAid, FileAid, Xpediter, CA-1, CA-7 & 11, MIM, Top Secret, Comparex, DYL, FDR, STK/HSC, InfoPac, JobScan, Omegamon, Panvalet, PGP Security.